Blog
September 12, 2023
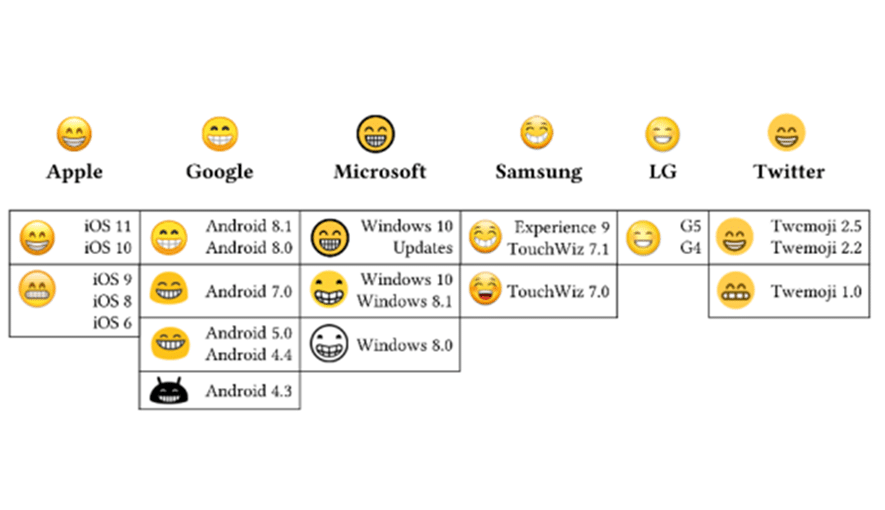
Emoji usage has grown significantly over the past few years since emoji characters provide people with the ability to express themselves in a clear and efficient way. These small, emotive characters—from ☂️to 😂 to 🤷 – represent the first language borne of the digital world that was originally designed to add emotional nuance to otherwise flat text.
November 18, 2021

2021 has been a record year for legal tech: $1.4 billion was invested by venture capital firms in the first half of the year, which is more than in the entirety of 2020, and well above what was raised in 2018 and 2019. Leading the investment boom are startups like RocketLawyer (which provides legal services to individuals and small businesses), Verbit (voice transcription for the legal sector), Notarize (digital notarization), and Clio (cloud based CRM).
January 7, 2020

Using Smarter AI via our KIBIT AI engine we then process your data set. This results in fewer documents, with greater relevance, for review. In turn, our clients spend significantly less time during the discovery review phase leveraging KIBIT Automator’s AI technology.
March 12, 2020

Parsing massive volumes of data for responsive documents within the often-restrictive timeframes imposed by litigation is challenging for any company. During eDiscovery, workflows must…
July 25, 2018

Economic integration in the ASEAN region, public investment, increased M&A activity, and the expansion of foreign and domestic multinational corporations are driving regional legal market…
December 14, 2022

One consistent message that seems to resonate from legislature to legislature across the world is the recognition of the fact that data - especially personal data - is both a weapon and a vulnerability, and in the quickly-evolving digital landscape of today the task of safeguarding it effectively becomes more and more difficult. The Australian legislature seeks to update its current privacy laws, which are based on both the original 1988 Privacy Act, and its later update from 2000, to reflect the rapid technological advancements that took place in the early 21st century in data collection, data storage and data analysis.
April 19, 2022

On April 4, the DOJ Antitrust Division announced an update to their leniency policy and issued a revised set of frequently asked questions (FAQ).
February 10, 2020

Exploding data volumes coupled with high costs have made the search for affordable, fast, and defensible eDiscovery technology a top priority for legal professionals.
July 24, 2020

Collecting electronically stored information (ESI) is a routine challenge for eDiscovery specialists, but one that’s becoming more and more complex as our technology environment evolves. The inherent difficulties of traditional ESI collection are compounded by…
August 28, 2020

If there was ever a single eDiscovery trend that everyone could agree on, it would without a doubt be the fact that data volumes in litigation grow year to year without fail.
November 7, 2019
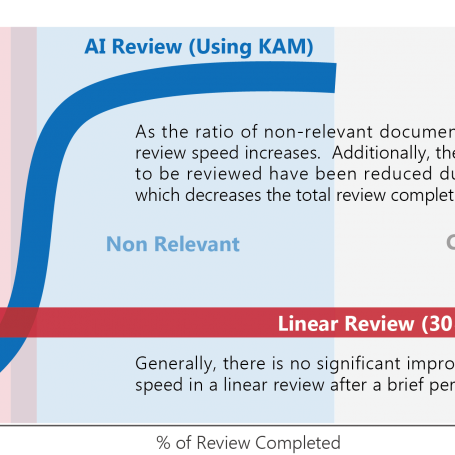
A more thorough and introductory explanation of this topic was originally featured on the ACEDS Blog. Attorneys often calculate recall and precision estimates based…
February 10, 2022

There is seemingly no limit to the applications for Artificial Intelligence and to the great expectations (or potential threats) that many tech and business leaders have predicted for its applications. In July of 2021 Google CEO Sundar Pinchai reiterated his belief that the effects and use of AI will be more profound on the history of humanity than fire or electricity, and Tesla founder Elon Musk has warned that AI could lead to the next world war. Nuclear fission is a common comparison among commentators, both in AI’s potential uses and potential dangers.
July 9, 2018

When discussion of bribery and corrupt business practices comes up, it’s common to think of China and Russia, and the high profile investigations in…
March 23, 2020

The Challenge A team of two attorneys faced a tight budget and an even tighter deadline. Close of discovery loomed, and extensive document review…
November 2, 2021
This is an opinion piece by FRONTEO data scientist in response to the article “US and EU New Guidelines and Views on AI” published on October 20th.
May 15, 2020

Part 1 In this two-part post we’ll look first at courts’ varied responses to the coronavirus (COVID-19) pandemic. Next time, we’ll examine the implications…
July 4, 2023

Privilege logs are a critical component of eDiscovery that requires careful planning, analysis and detail in order to successfully complete. This process can be costly and time-consuming as specific requirements tend to vary by jurisdiction and on a case-by-case basis. As such, in this blog we would like to provide a brief overview of the privilege log process, discuss various privilege log types used today, and review how existing technologies can be leveraged to achieve efficiencies when constructing a privilege log.
May 15, 2023

The legal industry is undergoing transformational changes as aspects of information governance and eDiscovery are refined with new data governance solutions and technologies to address evolving business and regulatory requirements.
October 26, 2021

October is the 18th Annual National Cybersecurity Awareness Month in the United States. It is sponsored by the Cybersecurity and Infrastructure Security Agency and the National Cyber Security Alliance. This year’s theme is “Do Your Part. #BeCyberSmart.” Being Cyber Smart includes awareness of current threats like business email compromise (BEC), phishing, ransomware, and supply chain compromise.
July 30, 2018

The ever-growing, complex web of privacy protection laws around the world directly impacts how multinational corporations can comply with demands to respond to a…
