Blog
November 18, 2021

2021 has been a record year for legal tech: $1.4 billion was invested by venture capital firms in the first half of the year, which is more than in the entirety of 2020, and well above what was raised in 2018 and 2019. Leading the investment boom are startups like RocketLawyer (which provides legal services to individuals and small businesses), Verbit (voice transcription for the legal sector), Notarize (digital notarization), and Clio (cloud based CRM).
July 9, 2018

When discussion of bribery and corrupt business practices comes up, it’s common to think of China and Russia, and the high profile investigations in…
October 20, 2021

The U.S. Federal Trade Commission (FTC) and the European Commission (EC) have issued guidance and opinions on AI. This guidance provides insight into how organizations can mitigate concerns and prepare for the future when using AI.
November 7, 2019
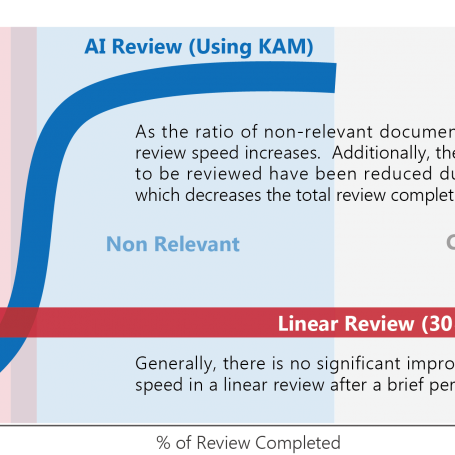
A more thorough and introductory explanation of this topic was originally featured on the ACEDS Blog. Attorneys often calculate recall and precision estimates based…
January 20, 2021

Technology Assisted Review (TAR) is now considered an essential tool in eDiscovery. Its popularity is, of course, closely tied to the increasing amounts of data used in litigation, especially when contrasted with the time, accuracy and cost of manual review.
July 24, 2020

Collecting electronically stored information (ESI) is a routine challenge for eDiscovery specialists, but one that’s becoming more and more complex as our technology environment evolves. The inherent difficulties of traditional ESI collection are compounded by…
October 26, 2021

October is the 18th Annual National Cybersecurity Awareness Month in the United States. It is sponsored by the Cybersecurity and Infrastructure Security Agency and the National Cyber Security Alliance. This year’s theme is “Do Your Part. #BeCyberSmart.” Being Cyber Smart includes awareness of current threats like business email compromise (BEC), phishing, ransomware, and supply chain compromise.
February 24, 2023

Bring Your Own Device (BYOD) programs remain both a major opportunity and challenge for enterprises. It is possible to capitalize on the benefits of BYOD without adding significant risk by following the right approach to identifying BYOD risk and developing an effective BYOD policy.
September 15, 2021

Antitrust against GAFA expected to continue in Biden administration (DOJ probes and lawsuits into GAFA)
November 26, 2021

Artificial Intelligence is a way of using technology to analyze large amounts of data in much less time than it would take a human user, and to make predictions based on this data that can be helpful for a variety of applications. Deep Blue’s legendary chess match against Kasparov is a classic example of AI and its ability to predict certain outcomes based on data.
October 24, 2019

Last year, Maruyasu Industries, an auto parts manufacturer of steel tubes, was fined $12 million for its role in a criminal conspiracy to fix…
July 30, 2018

The ever-growing, complex web of privacy protection laws around the world directly impacts how multinational corporations can comply with demands to respond to a…
June 4, 2020

By Joe Skalski Now that we’re well into the new work-from-home (WFH) norm, FRONTEO has been thinking about data preservation and spoliation. While we…
September 30, 2021

Legal departments rushed to transition their teams to work from home in order to adhere with the highest precautions.
August 5, 2020

COVID-19 has changed the pattern of peoples’ lives worldwide, and it has faced the legal profession with its own unique set of challenges. Not only must the justice system…
December 25, 2023
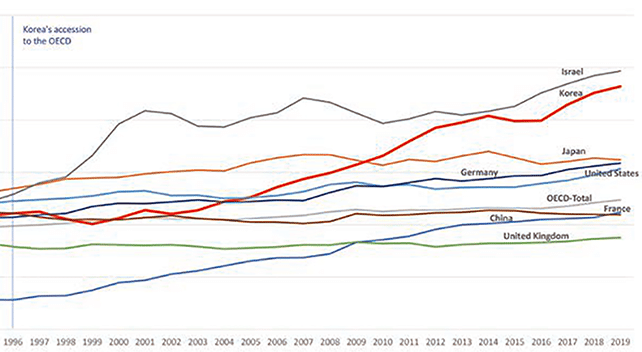
Global technology competition has grown fierce recently requiring nations to consider and enact technology protection policies and strategies. In Japan, for example, there was a significant change in 2014 under the Liberal Democratic Party that led to the development and passage of the Economic Security Promotion Act in 2022, along with a new National Security Strategy.
September 21, 2020

Technical Execution. The technical execution of a random sampling process is simple, quick and is fully supported in some eDiscovery platforms such as Relativity.
Let’s take a look at some of the main considerations and caveats to be aware of prior to utilizing this technique for validating your workflow.
November 2, 2021
This is an opinion piece by FRONTEO data scientist in response to the article “US and EU New Guidelines and Views on AI” published on October 20th.
July 4, 2023

Privilege logs are a critical component of eDiscovery that requires careful planning, analysis and detail in order to successfully complete. This process can be costly and time-consuming as specific requirements tend to vary by jurisdiction and on a case-by-case basis. As such, in this blog we would like to provide a brief overview of the privilege log process, discuss various privilege log types used today, and review how existing technologies can be leveraged to achieve efficiencies when constructing a privilege log.
March 20, 2023

Organizations in Japan, and generally across Asia Pacific (APAC), have experienced a sharp increase in eDiscovery related work over the past several years due to a rise in cross-border litigations and investigations. It is more critical now than ever before to take stock of important considerations when evaluating and partnering with service providers that will guide and support your eDiscovery needs.
