Who We are

At FRONTEO, we have both review and data scientist specialists who provide AI reviews using new technologies. In addition, our products are developed and serviced by a one-stop service, which allows us to provide high quality reviews at a reasonable cost compared to other companies' services.
Competitive Advantage of AI Review Solutio
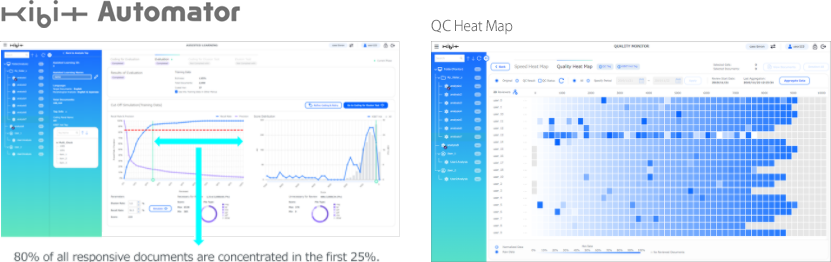
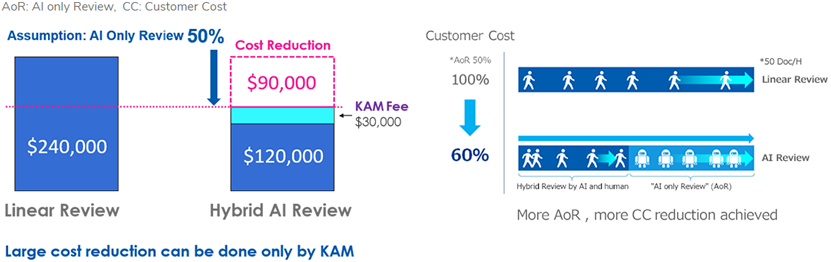
FRONTEO will make a paradigm shift from human review to AI review with a focus on KAM. FRONTEO has helped many clients with its unique AI solution. This can cut review time in half while improving the quality of the review and providing better control over the process. ( AoR: AI only Review, CoC: Cost of Customer)
Our AI-enabled services helps legal teams mitigate current and future legal risks.
- HOME >
- legal USA